What Is Identity and Access Management (IAM)?
IAM encompasses both the technological and administrative elements of an organization. On the technical side, the core components of IAM typically include:
- Identity data. This may include location details, access privileges, device information, and credentials, all stored in a centralized database. Where identity data is concerned, less is more — organizations should collect only what is necessary to identify a user accurately.
- Authentication. A means of ensuring an entity is who they claim to be. It is generally a combination of Single Sign On (SSO), Multifactor Authentication (MFA), Risk-Based Authentication (RBA), Behavioral Authentication, and user credentials.
- Management. IAM includes tools that facilitate the management of user permissions, roles, and privileges.
- Monitoring. IAM should include a means by which each entity’s behavior can be monitored, along with a means of enforcing additional validation.
The administrative side of IAM encompasses:
- Policies. A policy assigns permissions to an entity or role based on a set of predefined criteria. Policies may be either rules-based or dynamic.
- Permissions. Essentially, what users can see and do when they’ve been authenticated and authorized.
- Roles. A set of predefined permissions that apply to an entity.
It is important to note that IAM is a technology with a long history. However, legacy IAM controls like authentication challenges and password policies are ill-suited for today’s dynamic business environments. Modern IAM has shed its legacy trappings, embracing automation, the cloud, and Zero Trust Network Access (ZTNA).
Benefits of Identity and Access Management
As noted by Gartner, the benefits of IAM are currently not well-understood outside of a very narrow circle of specialized professionals. Understanding the benefits and how to express them to leadership is crucial in getting an IAM program off the ground. With that in mind, the benefits of leveraging IAM include:
- Improved productivity and collaboration
- Support for remote work
- Streamlined management of users and accounts
- Easier enforcement of security policies
- Improved regulatory compliance
- A stronger overall security posture
- Reduced IT costs
Compromised accounts and credentials have long represented one of the most significant threats to organizational security. IAM offers enhanced protection against this common threat vector, making it significantly more difficult for bad actors to access sensitive data even with stolen credentials. It represents an important additional layer of security for enterprise user accounts.
Additional IAM Benefits
- Dynamic security and access policies when paired with Artificial Intelligence (AI)
- Improved user experience
- Streamlined access control
- Better mitigation of insider threats
- Increased productivity
- Extend access to third parties such as contractors
How Identity and Access Management Works
At a high level, IAM fulfills the following tasks:
Identification. What claims is the user or entity making about their identity? Note that each entity and user must be assigned a unique set of credentials under IAM.
Authentication. Is the user or entity who they claim to be? Authentication may be fulfilled through a combination of the following factors:
- Type 1. Memorized credentials such as passwords and PINs.
- Type 2. Physical factors such as device ID or hardware tokens.
- Type 3. Biometrics or behavioral biometrics.
Authorization. Based on the user or entity’s identity, what privileges or permissions should they be granted?
Identity and Access Management Tools
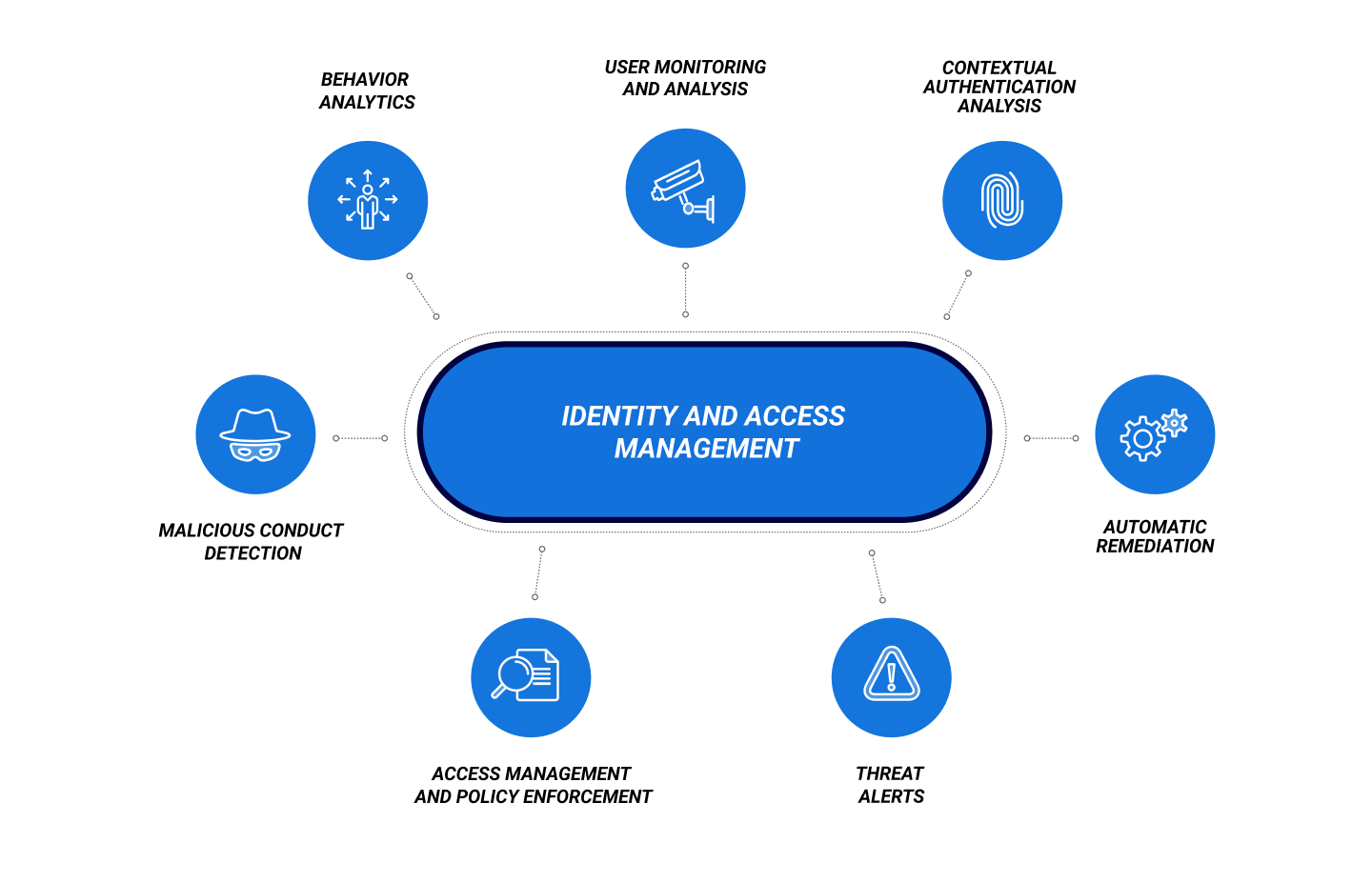
IAM tools are specialized solutions that bake all the functionality required from IAM into a single platform. Features of IAM software may include, but are not limited to:
- Behavioral analytics
- User monitoring and analysis
- Contextual authentication analysis
- Detection of anomalous or malicious conduct
- Access management and policy enforcement
- Threat alerts
- Automatic remediation
Identity Access and Management Best Practices
There are underlying ideas and concepts on which IAM is predicated. The efficacy of an IAM tool is typically measured by how it addresses these areas and principles:
Least Privilege
Users are only given access to the resources they require, and any identity data collected should be minimized as much as possible.
Continuous Authentication
In addition to leveraging multi-factor authentication and single sign-on, an effective IAM tool should continuously monitor and validate a user’s activities to ensure that they are who they claim to be. IAM tools might optionally leverage risk-based authentication.
Continuous Authentication validates users’ identity based on three primary categories:
- Credentials. Are the provided credentials valid? Has the user successfully provided all the necessary data for initial authentication?
- Behavior. Does the user display behaviors consistent with their established baseline?
- Activity. Is the user acting outside the scope of their typical duties or responsibilities?
Zero Trust
IAM has a close relationship with ZTNA and is a core enabler of the approach. Both are predicated on the notion that no entity should be implicitly trusted. Zero Trust also restricts access to individual resources rather than the entire network.
IAM vs UEBA
IAM vs SIEM
FAQ
What does IAM stand for?
IAM stands for Identity and Access Management.
What is an IAM tool?
IAM tools are software platforms designed to manage user identities, access, authentication, and authorization, merging all the technical aspects of IAM into a single solution.
What is the difference between IAM and UEBA?
UEBA is focused on monitoring and analyzing behavior, and IAM is concerned with using identities to control access to resources. The two are highly complementary.
What is the difference between IAM and SIEM?
SIEM solutions are focused on orchestrating and analyzing event data from across an entire organization. IAM focuses on authentication, authorization, and identity management, and the data it generates can be fed into a SIEM.
Why is IAM important?
IAM provides organizations with the flexibility, access control, and agility necessary to contend with a modern, distributed threat landscape. Authentication can no longer rely solely on passwords and devices—credential theft and impersonation remain the most successful threat vectors leveraged by attackers. IAM shields against this, automating the management of privileges while adding extra layers of authentication and validation.
Passwords alone can no longer protect your assets and are ill-suited for a dynamic, distributed environment. If you are to control access to applications and data without either impeding your users or putting your assets at risk, you need to embrace a user-centric, mobile-ware approach. You need IAM.
CylancePERSONA™ uses Machine Learning and predictive Artificial Intelligence to dynamically adapt and enforce security policies based on multiple factors, streamlining secure access while protecting against human error and insecure workarounds.