What Is the MITRE ATT&CK Framework?
MITRE is a government-backed not-for-profit organization that conducts federally funded cybersecurity research to support defensive IT security across all sectors, including government agencies and defense contractors.
MITRE ATT&CK® (Adversarial Tactics, Techniques, and Common Knowledge) is a free and open knowledge base of cybersecurity information first released in 2018. ATT&CK is designed to help cybersecurity analysts and others gain Cyber Threat Intelligence (CTI) insights for planning and designing cyber defense programs and facilitate communication by providing a common reference vocabulary.
MITRE ATT&CK Matrix
The complete MITRE ATT&CK framework is branched into three main variants, each containing a subset of TTP that applies to specific target IT environments. Each variant is known as a “Matrix.”
The three primary Matrices in the ATT&CK framework are the Enterprise Matrix, the Mobile Matrix, and the ICS (Industrial Control System) Matrix. The Enterprise and Mobile Matrices are further subdivided into sub-Matrices filtered to contain only those Tactics, Techniques, and Procedures (TTP) relevant to each environment.
Enterprise ATT&CK Matrix
Mobile ATT&CK Matrix
Industrial Control Systems (ICS) ATT&CK Matrix
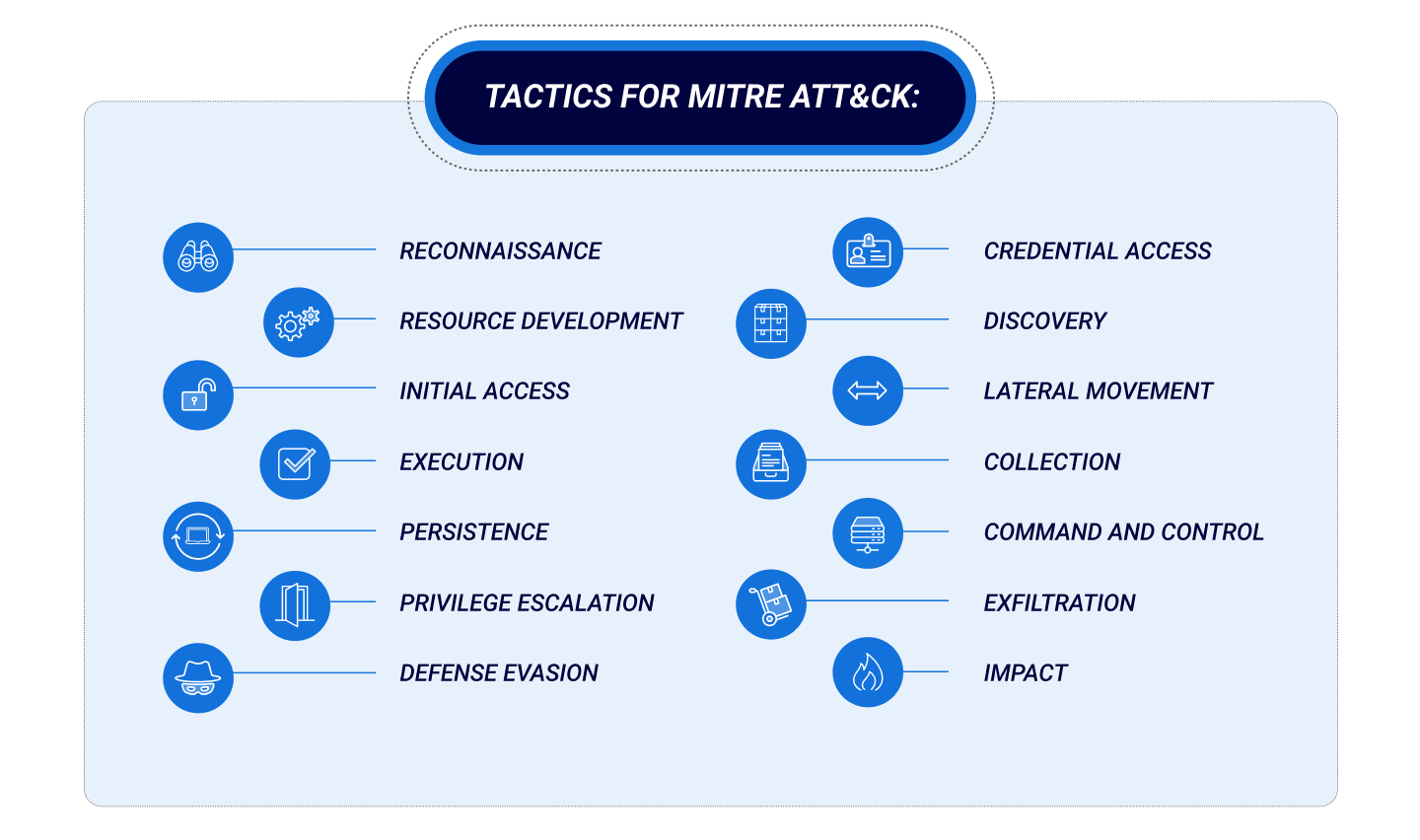
ATT&CK Tactics, Techniques, and Procedures
ATT&CK Tactics
- Reconnaissance (Enterprise, ICS)
- Resource Development (Enterprise, ICS)
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access (Enterprise, Mobile)
- Discovery
- Lateral Movement
- Collection
- Command and Control
- Exfiltration (Enterprise, Mobile)
- Impact
- Network Effects (Mobile-only)
- Network Service Effects (Mobile-only)
- Inhibit Response Function (ICS-only)
- Impair Process Control (ICS-only)
The Cyber Kill Chain® is a cyberattack framework released in 2011 by Lockheed Martin. Like MITRE ATT&CK, the Cyber Kill Chain categorizes all cyberattack behaviors into sequential tactics.
7 Stages of the Cyber Kill Chain
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control
- Actions on Objectives
The Cyber Kill Chain is fundamentally different from the MITRE ATT&CK framework in that it claims all cyberattacks must follow a specific sequence of tactics to achieve success; MITRE ATT&CK makes no such claim. Another difference between the two frameworks is that the Cyber Kill Chain is essentially a sequence of stages that comprise a cyberattack combined with a general defensive security axiom that “breaking” any phase of the “kill chain” will stop an attacker from successfully achieving their goal, and thus afford protection to the defender.
MITRE ATT&CK is much more than a sequence of attack tactics. It is a deep knowledge base that correlates environment-specific cybersecurity information along a hierarchy of Tactics, Techniques, Procedures, and other Common Knowledge, such as attribution to specific adversarial groups.
How to Use the MITRE ATT&CK Framework
MITRE ATT&CK Use Cases
Threat hunters, red teamers, and defenders use ATT&CK for insights into cyberattacks and a standard classification system that can be used as a reference for communication between stakeholders when developing enterprise cybersecurity programs.
Because it is a comprehensive knowledge base of cyberattack information, ATT&CK can serve as a checklist of attack goals and methodologies. You can use this checklist to justify implementing security controls, ensuring they are comprehensive and offer some degree of protection against all elements that comprise real-world cyberattacks.
ATT&CK can also be used by penetration testers, red teams, and security product testers to emulate realistic cyberattacks. ATT&CK enables simulated adversaries to understand the attack landscape and apply the same tactics and techniques as real-world attackers.
FAQ
What Does MITRE ATT&CK Mean?
ATT&CK stands for Adversarial Tactics, Techniques, and Common Knowledge.
What is the MITRE ATT&CK Framework?
MITRE ATT&CK is a free and open knowledge base of cyberattack strategies and related information designed to help cybersecurity analysts and other stakeholders gain Cyber Threat Intelligence (CTI) insight and facilitate communication about offensive and defensive cybersecurity.
What is the MITRE ATT&CK Matrix?
The MITRE ATT&CK Matrix is a hierarchical framework of attack tactics and techniques that comprise cybercriminals’ individual goals and strategies. There are three primary ATT&CK Matrices, each addressing distinct environments: Enterprise, Mobile, and Industrial Control Systems.
BlackBerry’s suite of Cylance cybersecurity solutions was 100 percent successful in preventing both the Wizard Spider and Sandworm attack emulations very early in MITRE ATT&CK's 2022 evaluation—before any damage occurred.
BlackBerry’s CylancePROTECT® and CylanceOPTICS® solutions provided comprehensive detections on individual attack techniques with high confidence, helping to reduce wasted resources spent chasing false positives.