What Is User and Entity Behavior Analytics?
User and Entity Behavior Analytics (UEBA) is an algorithmic approach to network monitoring that focuses on the activities of both human actors and entities such as hosts, software platforms, and endpoints. Through machine learning, UEBA solutions establish a baseline for what constitutes ‘normal’ behavior on a network. They then use this baseline to identify potential threat actors and compromised systems.
Threat actors rarely leverage a single compromised account when launching an attack. Their tactics are frequently designed to confound security that focuses on static rules. Insider threats are especially difficult to detect with a legacy solution as their behavior can simply look like someone doing their job.
Finally, rules-based security solutions are ill-suited for the dynamic, perimeterless ecosystem in which most of us now operate.
UEBA evolved as a response to these challenges. With its focus on real-time behavior rather than predefined flags, it allows businesses to detect possible threats faster and more accurately. Together with Endpoint Protection and Extended Detection and Response, UEBA is an important component of Zero Trust Network Access, providing the necessary support for processes such as continuous authentication.
Benefits of UEBA
The benefits of adopting UEBA include:
- Reduced workload for security teams
- Reduced alert fatigue
- Lower overhead
- Better protection against insider threats
- Management/monitoring of cloud and IoT assets
UEBA doesn’t rely on static rules or signatures, making it better equipped to protect against zero-day threats and unknown attack patterns. This also makes life significantly easier for security teams. Instead of having to spend time painstakingly configuring rules for every possible scenario, they can focus on mitigation and response.
Because UEBA is built on machine learning, solutions grow progressively more accurate at identifying whether an action is normal or suspicious. This results in fewer false positives and lower overall notification volume. Additionally, internal threat actors are far more easily detected through behavioral analytics, meaning UEBA also offers improved protection against both malicious insiders and carelessness.
Additional UEBA Benefits
- Adaptive, dynamic security policies
- Faster time to detection of advanced threats
- Increased accuracy of detection
- Greater control over security policy
- Better security for contractors and remote staff
- Detection of non-malware-based attacks
How UEBA Works
UEBA is built on baselines. The core idea is that even if a threat actor manages to compromise someone’s account, they cannot mimic that individual’s behavior—their actions will deviate from what constitutes ‘normal.’ Similarly, if an insider suddenly begins behaving in an abnormal fashion, a UEBA tool can flag that activity for investigation.
UEBA doesn’t solely focus on users, however. It also analyzes the behavior of non-human entities on the network such as endpoints and software platforms. Some UEBA solutions further extend their focus to include events.
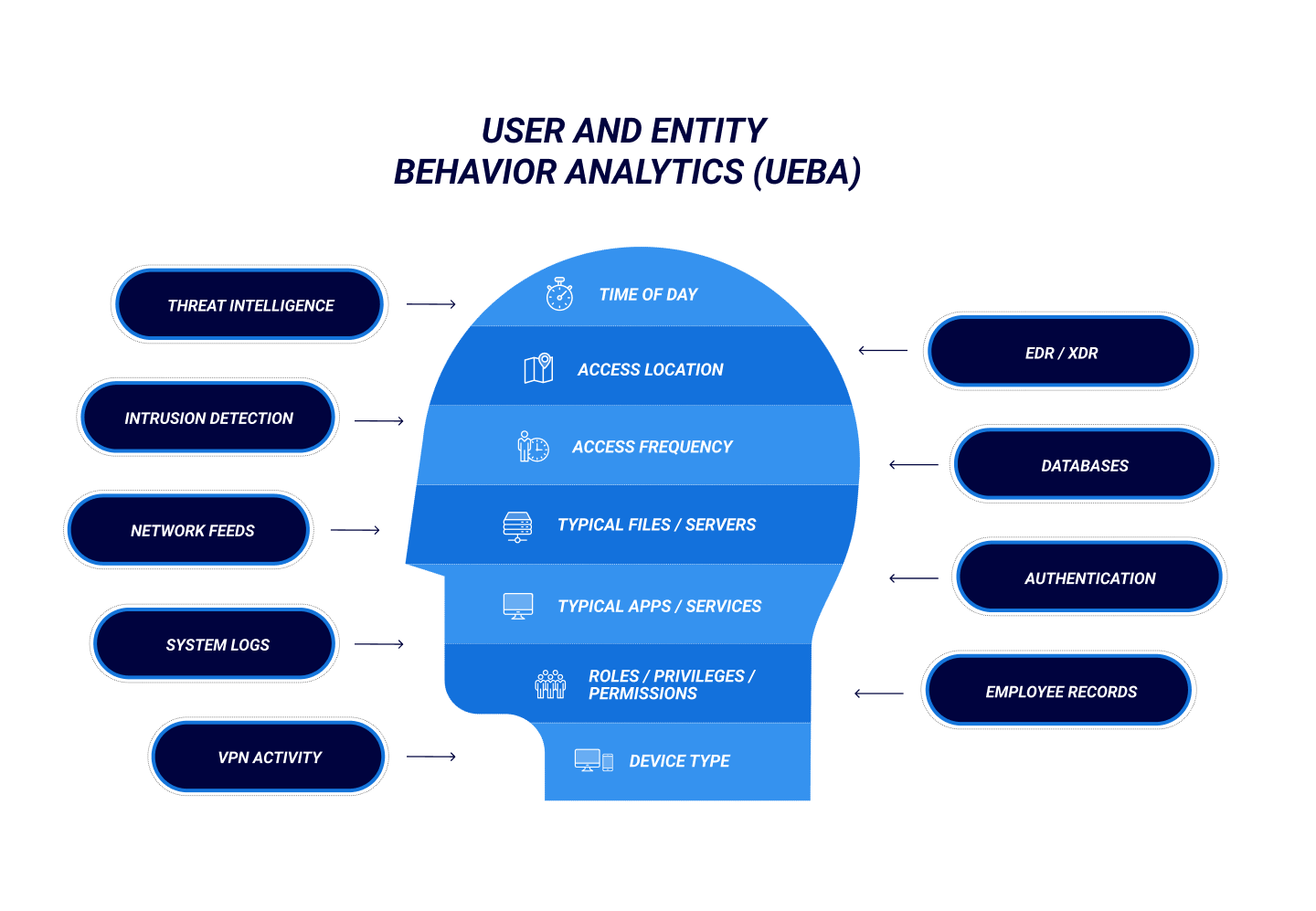
Whatever its scope, a UEBA solution analyzes a multitude of data sources to establish its baselines:
- Threat intelligence
- Intrusion Detection and Prevention Systems (IDPSs)
- Network monitoring feeds
- System logs
- VPN activity
- EDR or XDR systems
- Databases
- Authentication systems
- Employee records
Relevant data drawn from the above includes:
- Access location
- Time of day
- Frequency of access
- Typical files or servers
- Typical applications or services
- Roles, privileges, and permissions
- Device type
Once this information has been fully digested and contextualized, the UEBA then defines a risk score for each user and entity. Whenever any activity occurs that deviates from the baseline, that score increases. Eventually, once that score reaches a predefined threshold, the user or entity is brought to the attention of the security team.
Some advanced UEBA solutions can even orchestrate and aggregate data from multiple systems to construct a timeline of a security incident or disruptive event. This a process is known as session stitching.
The “Three Pillars” Of UEBA
Use Cases
Data Sources
Analytics
Best Practices for Implementing UEBA
The following steps are crucial in building an effective baseline and successfully implementing UEBA into your cybersecurity posture:
- Understand your organization’s risk profile.
- Determine how you intend to use UEBA—what use cases will this deployment address?
- Identify the data sources your UEBA solution will use.
- Define which behaviors are relevant to your use cases.
- Determine who will receive UEBA notifications, and when.
- Account for both internal and external users and entities.
- Ensure your processes and policies align with your adoption of UEBA.
- Test your UEBA solution regularly and comprehensively.
UEBA Use Cases
Detection of Malicious Insider Threats
Defending against Advanced Persistent Threats
Advanced persistent threats and unknown threats are incredibly difficult to detect and mitigate. They frequently follow a complex kill chain, featuring tactics or behavior not yet identified as dangerous. UEBA makes it far easier to identify when a trusted user, account, or device has been compromised, as they will inevitably behave in a manner outside their baseline.
It can also be applied to detect when someone with privileged access is careless with sensitive assets.
Preventing Data Exfiltration
Management and Prioritization of Alerts and Incidents
UEBA vs. SIEM
Given their similarity of purpose, one may be tempted to view Security Incident and Event Management (SIEM) as mutually exclusive to UEBA. This is not an accurate assessment. Although there may be some overlap in use cases, UEBA and SIEM solutions serve different purposes.
And they work very well in tandem.
This is perhaps why Gartner views UEBA as an extension of SIEM, rather than as a separate technology. It’s not difficult to see why this is the case. The two very much compliment one another, with the SIEM solution serving as a valuable source of data for the UEBA tool and the UEBA tool offering more sophisticated threat detection and analysis.
FAQ
What does UEBA stand for?
UEBA stands for User and Entity Behavior Analytics.
What is UEBA security?
UEBA solutions augment existing cybersecurity practices and processes through sophisticated machine learning. When paired with ZTNA, XDR, and EPP, it comprises a more modern, complete approach to security and business continuity.
What is a UEBA tool?
A UEBA tool is any software or platform with built-in UEBA functionality. It may be either pure play (completely dedicated to UEBA), or embedded (UEBA is included as part of overall functionality).
What is an “entity?”
In the context of UEBA, an entity is any non-human element capable of acting—either autonomously or at the direction of a human actor—upon a network. These include, but are not limited to:
- Endpoints
- Software and applications
- Mobile devices
- Other networks or organizations
- IT systems such as network hardware
- Non-human threats (i.e.. ransomware, malware)
- Other businesses
What is the difference between UEBA and UBA?
UBA (User Behavior Analytics) focuses on human actors only. UEBA, on the other hand, analyzes the behavior of the devices and machines on a network in addition to that of users. UEBA also places a greater focus on external threats than UBA.
This aside, the two are nearly identical.
What are the three pillars of UEBA?
The three pillars of UEBA, as defined by Gartner, are the core functions a UEBA solution or framework should adopt in order to be effective. These are:
- Use Cases. UEBA must define and address multiple distinctive use cases
- Data. A UEBA solution should be capable of ingesting data from multiple predefined data sources such as data lakes, data repositories, or via a SIEM without dedicated instrumentation agents.
- Analytics. UEBA requires a relatively complex approach to algorithmic cybersecurity, leveraging multiple threat modeling and machine learning techniques such as statistical models, rules-based monitoring, behavioral analysis, and threat signature detection.
What is the difference between UEBA and SIEM?
Security Information and Event Management (SIEM) tools aggregate and contextualize system event data to enable more effective real-time management of active threats. UEBA focuses more on behavior than events, allowing it to detect more sophisticated attacks that a SIEM might overlook. It is important to note that UEBA and SIEM are not mutually-exclusive—Gartner actually considers UEBA to be a feature of modern SIEM platforms.
Why is UEBA important?
Business operating environments are increasingly complex and dynamic—configuring rules-based security systems to adhere to such an ecosystem is untenable at best. More importantly, modern threat actors are clever. Their tactics are frequently designed to confound prevention-focused legacy security solutions.
UEBA also plays an important part in Zero Trust Network Access (ZTNA) and helps a business reduce false positives and unnecessary alerts.
Workforces have become more dynamic and adaptive than ever. We no longer live in a world where organizations can rely on static, rules-based security solutions—they need tools that are more agile, dynamic, and adaptable.
BlackBerry can help. As part of BlackBerry Spark® Suites—our complete solution—CylanceGUARD™ combines machine learning and advanced predictive artificial intelligence to dynamically define and adjust security policy based on how and where users work. Through CylancePERSONA, you can empower your employees to work however and wherever they see fit—while still keeping your most sensitive and important assets safe.