BlackBerry Named 2023 Customers’ Choice for Endpoint Protection Platforms on Gartner Peer Insights
Trusted Experts. Proven AI. Expansive Portfolio.
The complexity of Security and IT Ops, along with limited resources and increasingly sophisticated threats, make it progressively harder to focus on running your day-to-day business. Read the solution brief to learn how BlackBerry Cybersecurity driven by Cylance AI can help.



AI-Driven Security



Broad, Integrated Controls

Extension of Your Team
Achieve a Higher-Level Security With Cylance AI
Award-Winning Cybersecurity
BlackBerry® solutions with Cylance® AI have been honored with a variety of industry awards.
Bluebird is a trusted name. To maintain that trust, we needed to make sure our security was bulletproof. BlackBerry software, coupled with managed security and response, was the perfect solution for us to do so.
Muhammad Suhada, Former Vice President of Information Technology, Bluebird Group
By setting up Zero Trust, we eliminated almost a million dollars worth of spend simply because we no longer needed a security operations center monitoring our endpoints. Our data is safe, and our assets are walled off and protected. We were recently targeted by zero-day ransomware — CylancePROTECT stopped it in seventeen milliseconds.
Collin Buechler, Information Security, Data Privacy & Compliance officer, ConvergeOne
Onboarding and deployment was easy. The BlackBerry team was great with detailing what the daily administrative load would entail, which is not much, and after the first couple of weeks where you "train" the product to your environment, it runs without much nannying at all. Support is prompt and friendly. I really think that BlackBerry's status does not reflect how good an offering this is, and it suits us (a manufacturing company) very well, for not that much money.
Anonymous, Manufacturing Company
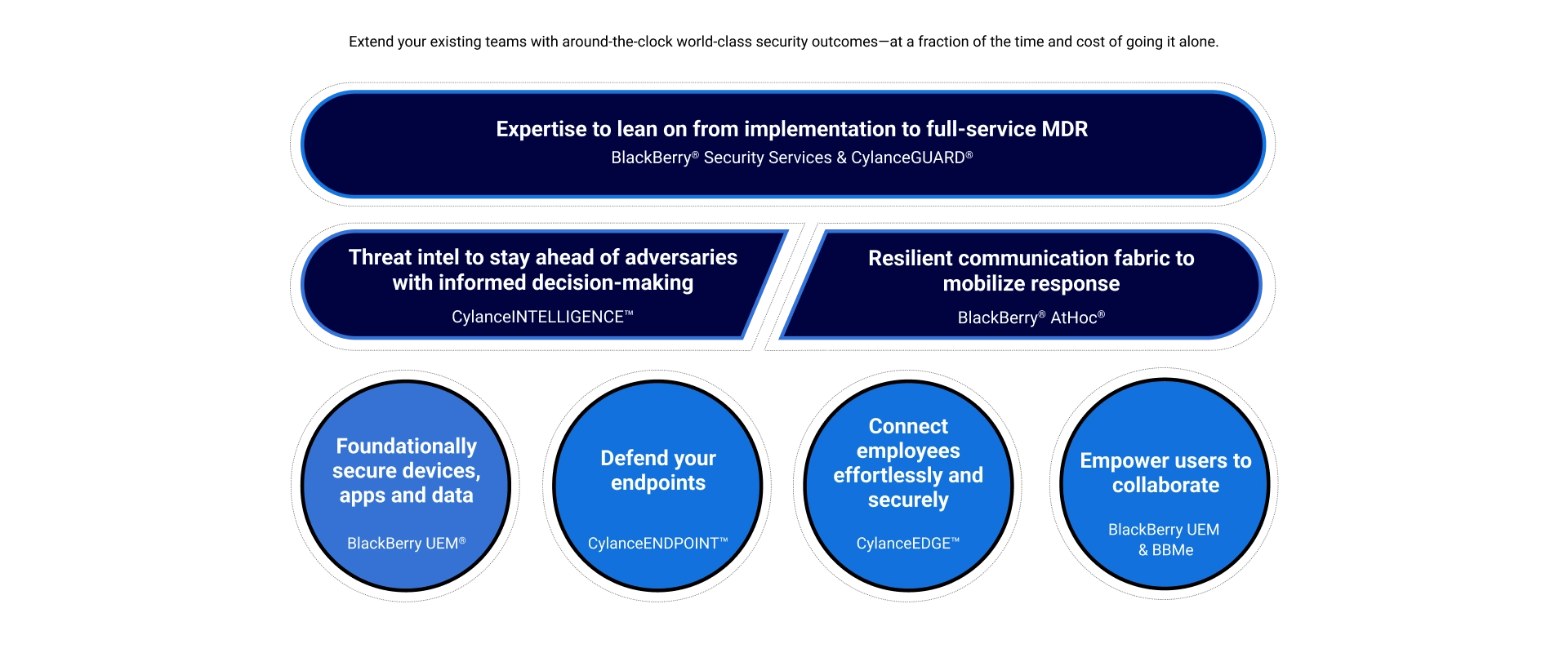
Diverse Platform, Strong Defense
BlackBerry can work with your team across all levels and skillsets to assemble the right combination of products and services specific to your environment to defend against a variety of threats.



CylanceENDPOINT



CylanceEDGE



CylanceINTELLIGENCE



CylanceGUARD