What Is Endpoint Detection and Response?
According to Gartner, an Endpoint Detection and Response (EDR) solution “stores endpoint-system-level behaviors, uses various data analytics techniques to detect suspicious system behavior, provides contextual information, blocks malicious activity and provides remediation suggestions to restore affected systems.”
An EDR solution must provide these four primary capabilities:
1. Detect Security Incidents
2. Contain the Incident at the Endpoint
3. Investigate Security Incidents
4. Provide Remediation Guidance
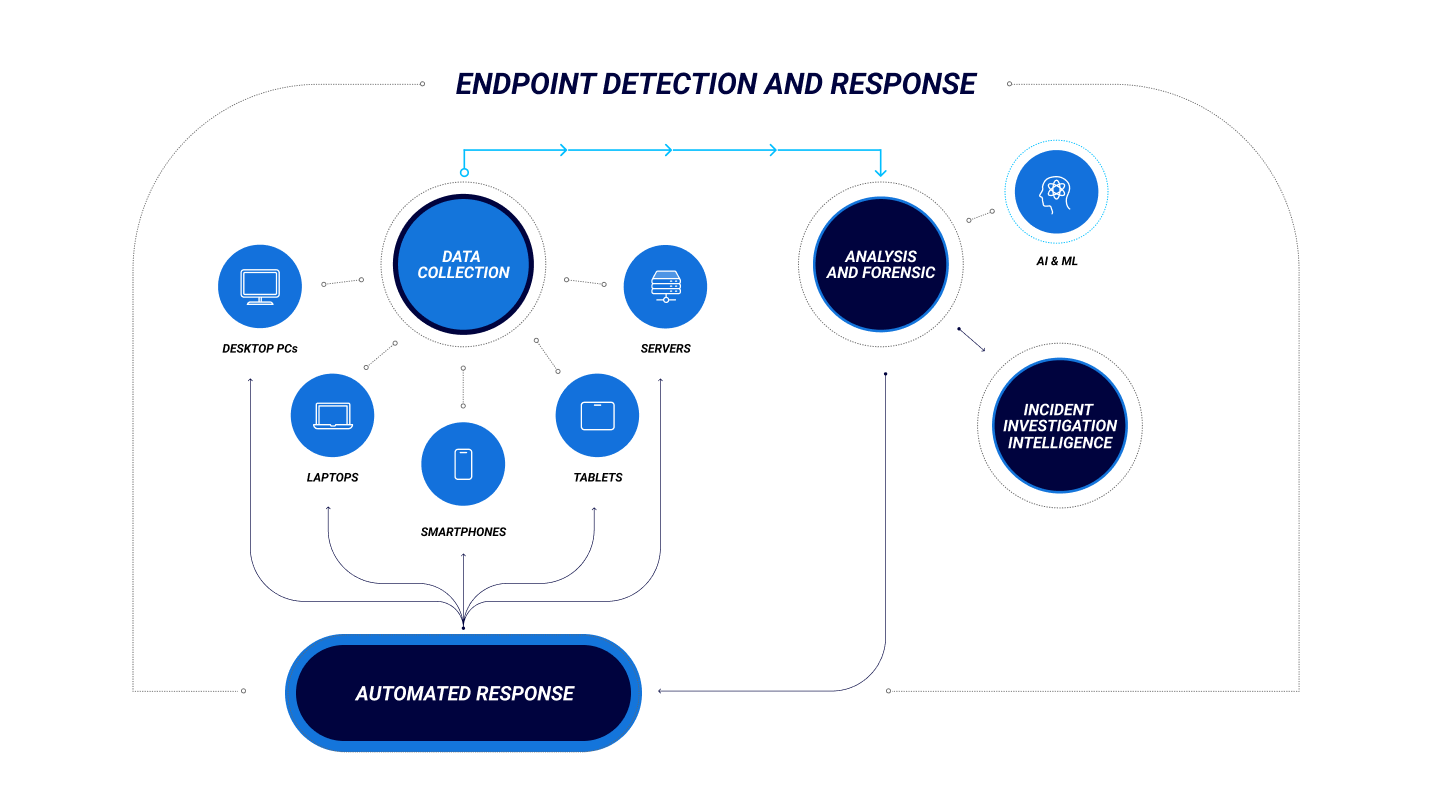
EDR Features
To effectively detect, contain, analyze and remediate from a cyberattack, an EDR solution should include various tools:
Endpoint data collection agents that monitor and collect data regarding file transfers, processes, activity and connections into a central repository for analysis.
Automated responses integrated within the network’s systems to act based on preconfigured rules, such as to log off a user and alert the security team when there is a known type of breach.
Analysis and forensics, with both real-time analytics to triage potentially malicious events and forensics tools for threat hunting and a post-mortem following an attack.
According to Gartner, an effective EDR solution should also have these advanced features:
- A combination of modern prevention techniques with detection and response capabilities
- A single lightweight agent
- A cloud-hosted infrastructure
- Unification of many tools in one console with additional integration options
AI and ML are increasingly important features of effective EDR because many cyberthreats evolve more quickly and strike before an signature-based EDR solutions can update to identify and contain them. AI-driven EDR can find cyberthreats that humans alone cannot.
Benefits of EDR
Improved Visibility
Faster Remediation
Optimized Threat Hunting
FAQ
What is EDR?
Endpoint Detection and Response (EDR) is a cybersecurity solution that involves continuous monitoring of and gathering data from endpoints to discover and address cyberthreats in real time. EDR extends on the capabilities of an Endpoint Protection Platform (EPP) by proactively identifying cyberthreats and preventing widespread security incidents.
What is an EDR system?
An EDR system or solution is an on-premises, cloud-based or hybrid software platform that monitors network endpoints for security incidents and can identify and respond to cyberattacks as well as provide contextual information to security teams for advanced threat hunting.
Is XDR better than EDR?
Although EDR is an effective defense against cyberattacks, XDR expands on EDR with additional protections at the network, servers, cloud and application levels. Both EDR and XDR involve continuous monitoring, threat detection and automated response to cyberthreats, but EDR’s scope is generally limited to endpoints while XDR is more comprehensive.
The global shift to remote work arrangements has increased cybersecurity risks beyond experts’ initial estimates. To address the growing number and severity of cyberthreats, CISOs and security analysts must look beyond traditional EDR solutions and start thinking in terms of XDR. Although securing endpoints is critical for protecting the corporate environment, today’s expanded workplace demands holistic solutions that include network telemetry, behavioral analysis and continuous authentication.
Cloud-native CylanceOPTICS® provides on-device threat detection and remediation across your organization—in milliseconds.