What AI-Driven EDR Can Do for You
To be sure your endpoints aren’t the weak link against cyber threats, it’s time to embrace the new approach to EDR, built on a strong artificial intelligence (AI) foundation and rooted in threat prevention. Are you ready for smarter EDR?
A New Approach To EDR



Get the Whole Story
When a threat is thwarted, security staff must be able to capture critical data and perform a root cause analysis to understand the origin of the attack and how an attacker attempted to compromise the endpoint.



Visibility Informs Action
If a computer behaves irregularly or it is determined that an endpoint may be at risk of compromise, an organization’s security toolkit must deliver the visibility required to make definitive judgments.



Expose Hidden Threats
Take the next step, locate, and expose hidden threats where they can be mitigated. Long considered a task for elite security analysts, AI-driven EDR simplifies the process, making it available to every member of your security team.
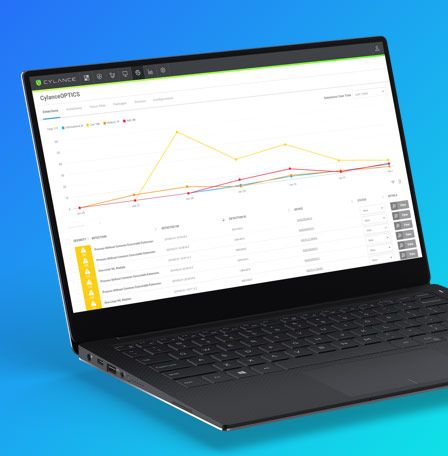
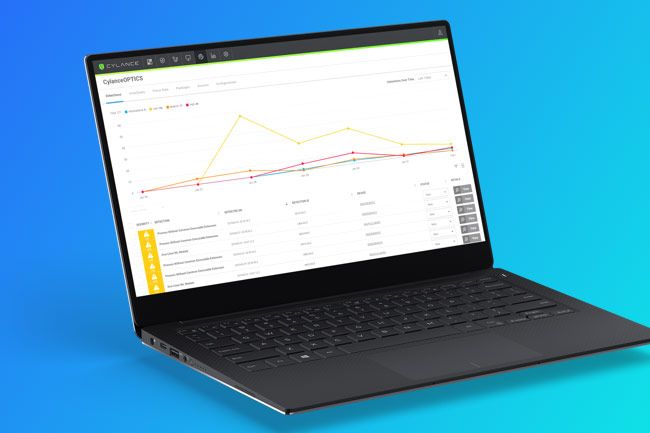

Automate Threat Detection
To root out threats before they can cause serious damage, an automated approach to threat detection that combines static, machine learning, and custom rules is required to identify and block advanced threats.
Traditional EDR vs. AI-Driven EDR: A Comparison
| Benefit | CylanceOPTICS | Traditional EDR |
|---|---|---|
|
A prevention-based approach reduces the overall number of incidents that require action/analysis
|
||
|
A solution accessible to all widens the pool of possible talent who can manage the solution
|
||
|
Collecting only security-relevant activity data locally significantly reduces liability and improves compliance
|
||
|
Storing data locally significantly reduces liability, improves compliance, and optimizes performance and scalability
|
||
|
Eliminates the need for up to thousands of rules that must be created and maintained by a security expert
|
||
|
Increases your ability to uncover hard-to-find threats without adding staff
|
||
|
Automated approach shortens time to analysis completion
|
||
|
Automation and machine learning allow organizations big and small to maintain the security posture once thought only available to the largest of organizations
|

Extend and Augment Your Security Strategy with the BlackBerry Consulting Team
While CylanceOPTICS® automates the threat detection and response processes, the BlackBerry consulting team of experts can help you identify and mitigate threats even faster with fewer resources, while our ThreatZERO white-glove service offers dedicated support for all of our solutions.
Don’t Take Our Word for It
C-suite and IT professionals across every industry are looking to AI to bolster security at their enterprise.
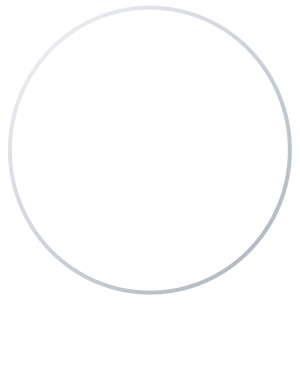
77% of security teams say AI-powered tools have prevented more breaches than non-AI tools
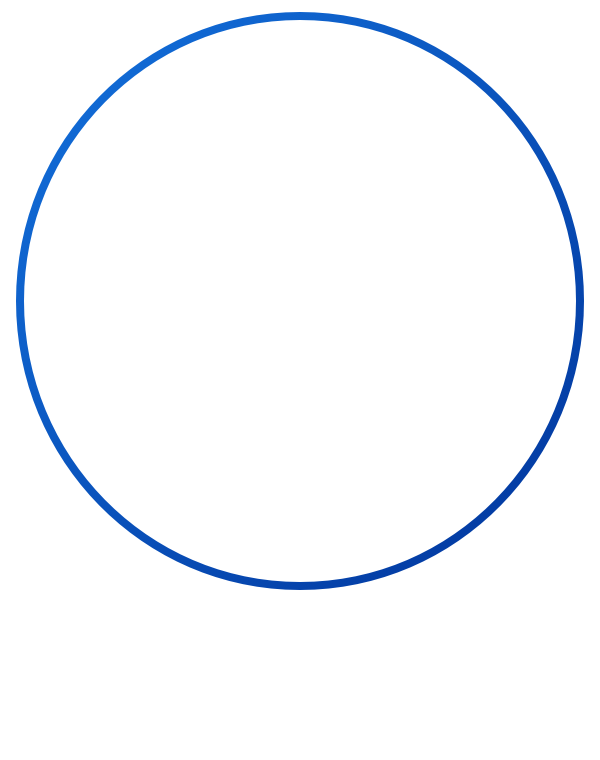
83% say that they are investing in AI to beat their competitors

78% of security teams say that AI has found threats that humans couldn’t see

80% say that teams that use AI have become more productive

2022 Threat Report
Read the BlackBerry® 2022 Threat Report to bring you up to speed on the latest techniques, tactics, and procedures (TTPs) used by cybercriminals, including advanced persistent threat (APT) groups. Use this information to help your organization allocate security resources wisely and protect against cyberattacks.
Learn More About What AI-Driven EDR Can Do for Your Organization



