What Is Zero Trust Network Access?
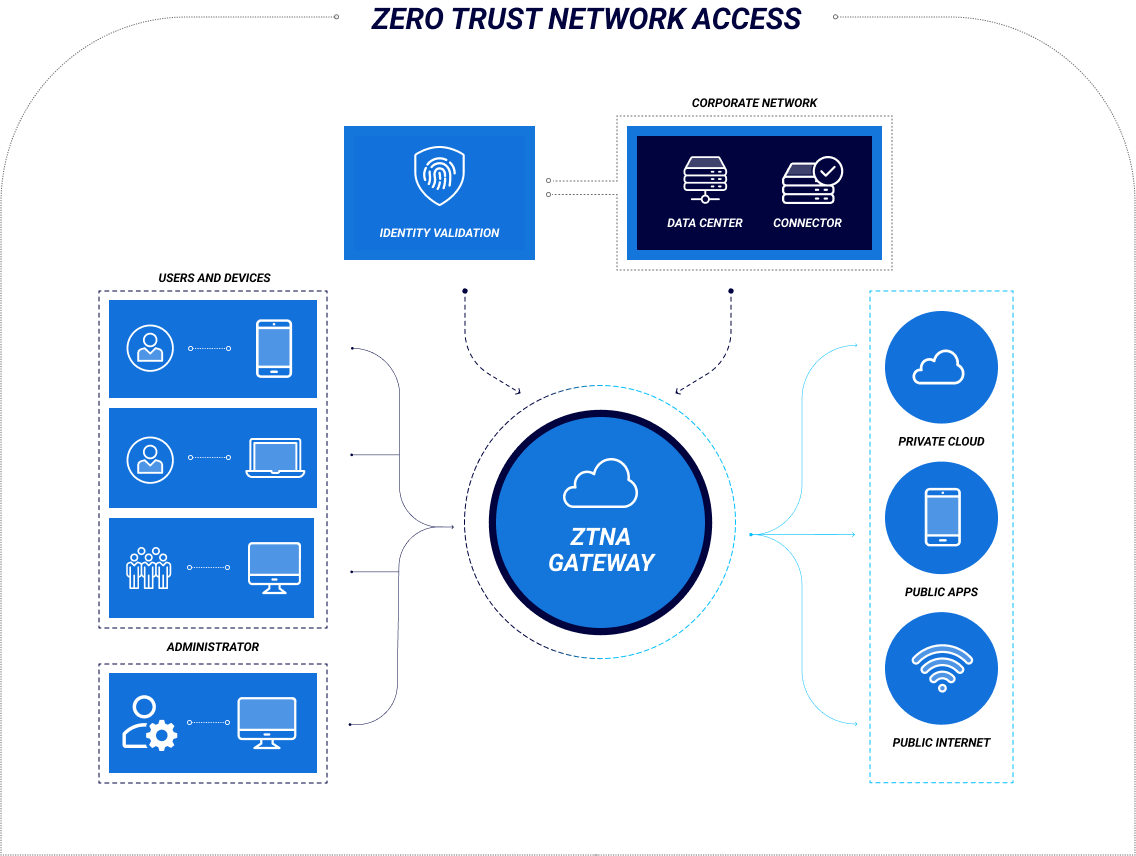
Zero Trust Network Access (ZTNA) is a security model that assumes every entity trying to connect to a network is potentially hostile. Under a ZTNA model, a user's role and permissions are irrelevant. If they wish to connect to internal applications or resources, they must authenticate and then continuously validate their identity—this is typically achieved via strict access controls combined with contextual and behavioral flags.
ZTNA emerged as a necessary response to highly distributed networks and supply chains. As businesses continue to scale their ecosystems, directly controlling every device and endpoint becomes increasingly infeasible. Similarly, extending unrestricted access to remote users in this climate has the potential to directly expose a network to an array of threats and threat actors.
Benefits of ZTNA
According to Forrester, the benefits of adopting ZTNA include:
- Improved network visibility, vulnerability management, and breach detection
- Prevention of malware propagation
- Reduced capital and operational cybersecurity expenditures
- Reduced scope and cost for compliance initiatives
- Improved interdepartmental collaboration during disruptive events
- Enhanced insight into and awareness of data as it flows through the network
- Protection against data exfiltration by threat actors
- A strong basis for digital business transformation
Because it provides direct, segmented access to applications and services, ZTNA is inherently secure. It dramatically reduces a business’s potential attack surface, as threat actors can no longer move laterally within the network. It also lays the groundwork for migration from Endpoint Detection and Response (EDR) towards Extended Detection and Response (XDR).
The most significant benefit of ZTNA by far, however, involves the end users. A business that adopts and integrates ZTNA with strong Endpoint Security can ensure only valid users and healthy devices are granted access. This allows the business to support both BYOD and remote work initiatives without exposing sensitive assets to undue risk.
Additional ZTNA benefits:
- Improved network speed and performance
- Better end-user experience
- Extensive scalability without the need for additional hardware
- Easier policy management
ZTNA Features
ZTNA is more of a network model than it is a reference to any specific technology. It applies the principles of the Zero Trust model of cybersecurity as defined by NIST 800-207 to network access. Any business that seeks to embrace ZTNA should ensure that it’s capable of the following:
- Continuous verification and validation of access privileges for all resources
- Dynamic access policies that can be adjusted based on user behavior
- Real-time visibility of the business’s entire ecosystem
- Centralized management of all security controls
- Extended Detection and Response, ideally supported by cybersecurity AI
- Identity and Access Management
- Multi-Factor Authentication (MFA)
- Security auditing and reporting
How ZTNA Works
Traditional network access is based on two principles:
- Trust, but verify
- All users and endpoints within the network are trusted by default.
Unfortunately, this approach is predicated on the idea that a business’s security perimeter not only exists, but can also prevent unauthorized access. In a landscape defined by cloud computing and hybrid work, neither concept holds true. The traditional firewall-based perimeter has dissolved.
ZTNA functionally replaces it with a new, more dynamic perimeter. Per Gartner, ZTNA involves the creation of “an identity- and context-based, logical access boundary around an application or set of applications.” Access is restricted to a set of specific named entities via a trust broker. In this way, said applications are hidden from discovery, simultaneously reducing a business’s attack surface while preventing lateral movement.
ZTNA is built on five key principles:
- Continuous monitoring
- Ongoing validation
- Least-privilege access
- Microsegmentation
- Device and endpoint authorization
Use Cases for ZTNA
Access Control and Authentication
ZTNA primarily exists as an alternative to the IP or account-based access controls used in legacy remote access solutions such as virtual private networks (VPNs). By defining and applying strict rules and standards around access permissions, businesses are able to configure and control access on a granular level. Potential options in this regard include:
- Preventing connection requests from unpatched devices.
- Not allowing users to authenticate if they aren’t running approved security software.
- Providing different permission levels to personal devices vs. corporate devices.
- Modifying permissions based on user location.
Supply Chain Management
Distributed Cybersecurity
In many ways, ZTNA represents an evolution of VPN technology. VPNs were built for a different time, back when businesses had well-defined security perimeters and did not have to contend with constantly evolving ecosystems. As a result, VPN technology has numerous drawbacks when compared to ZTNA solutions.
- Security. A VPN extends a business’s network to a remote user, allowing them to step inside the entire security perimeter rather than a granular, tightly controlled segment.
- Performance. VPN connectivity is typically marred by heavy resource utilization, cumbersome interfaces, and high latency.
- Ease of configuration. VPN software is not designed with flexibility or agility in mind. Adapting security policies and controls based on context thus tends to be incredibly difficult.
FAQ
What does ZTNA stand for?
ZTNA stands for Zero Trust Network Access, a security model that assumes every entity trying to connect to a network is potentially hostile.
What is ZTNA?
Zero Trust Network Access is a security model that assumes that all users, endpoints, and entities are hostile by default, requiring validation and authentication.
What’s the difference between ZTNA and VPN?
ZTNA software is more lightweight, flexible, and agile than VPNs. They are also built for granular access and segmentation rather than extending the entire network to any authenticated user.
Learn MoreWhy is ZTNA important?
The traditional security perimeter no longer exists, and legacy network security tools can no longer effectively control access. This is especially true for businesses that wish to embrace digital transformation. They need a level of agility, flexibility, and segmentation that older solutions like VPNs simply don’t provide.
What does ZTNA have to do with SASE?
Secure Access Service Edge (SASE) is essentially the convergence of multiple security and networking services and concepts into a single, unified platform, typically delivered via the cloud. ZTNA is typically viewed as a crucial component of SASE.
CylanceGATEWAY™ is AI-empowered Zero Trust Network Access (ZTNA). It allows your remote workforce to establish secure network connectivity from any device—managed or unmanaged—to any app in the cloud or on premises, across any network. This cloud-native ZTNA solution provides scalable outbound-only access to any application while hiding critical assets from unauthorized users—minimizing attack surface areas.
The multi-tenant architecture of CylanceGATEWAY is designed for digital transformation and distributed work. Its powerful AI and machine learning improve your security posture and simplify the configuration and management of granular, dynamic security policies and access controls.