What Is the Cyber Kill Chain?
The Cyber Kill Chain®, developed by Lockheed Martin, is a list of stages in a cyberattack that threat actors must complete in order to achieve their objective. By identifying an attack's stage of progress, an organization can better defend against and stop a cyber incident.
Though the Cyber Kill Chain was introduced more than a decade ago, many organizations still use it to help define their cybersecurity processes.
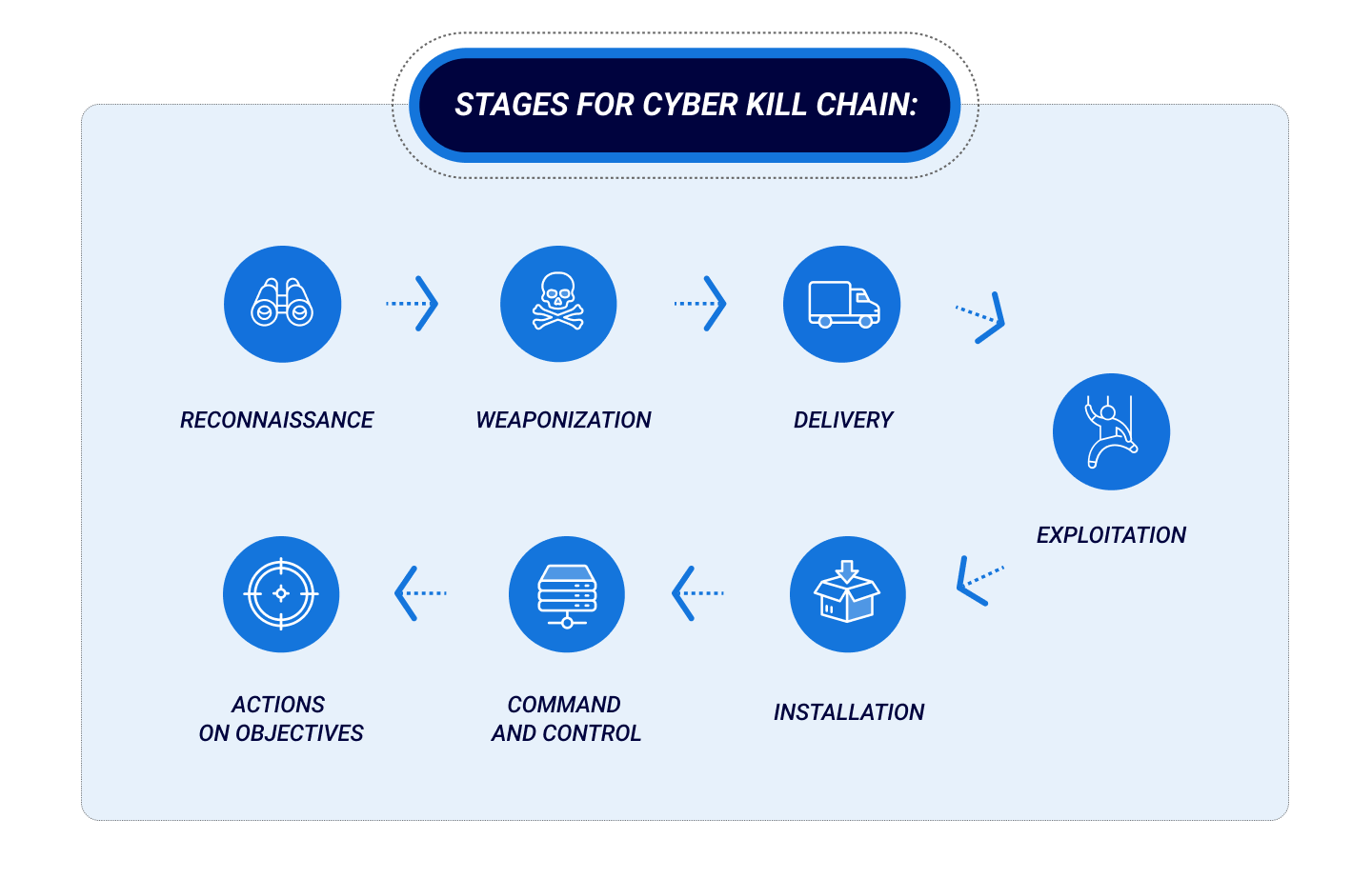
Stages of the Cyber Kill Chain
1. Reconnaissance
2. Weaponization
3. Delivery
4. Exploitation
5. Installation
6. Command and Control (C2)
7. Actions on Objective
How to Use the Cyber Kill Chain
The Cyber Kill Chain can help organizations establish a cybersecurity strategy to withstand attacks. It shows organizations the different levels of an attack and where security may be lacking.
As a part of the Cyber Kill Chain model, organizations should adopt security technologies to protect their network at each stage of the process. These solutions and services might include:
- Detection tools
- Preventative measures that keep unauthorized users from harvesting credentials
- Encryption to hide data being shared throughout the network
- Response tools and alerts that enable companies to respond to attacks in real-time
- Procedures to prevent lateral movement within the network
The Cyber Kill Chain provides cybersecurity teams with a framework to design their security ecosystem depending on their needs and vulnerabilities.
Evolution of the Cyber Kill Chain
As technology has evolved, so have the skills and abilities of threat actors. Cyberattacks are becoming more sophisticated—and more expensive for organizations to recover from. But the basic design of the Cyber Kill Chain remains the same.
Security experts criticize the Cyber Kill Chain model for its focus on perimeter security. Many organizations run on software-defined systems to enable collaboration and streamline data sharing, but the Cyber Kill Chain doesn’t address the needs of remote-work organizations or IoT devices and other endpoints that do not live on business networks.
It also doesn’t account for innovative threat actors’ various attack types and techniques. Web-based attacks, insider threats, and compromised credentials are unaccounted for in the Cyber Kill Chain model.
Cyber Kill Chain and MITRE ATT&CK® are both frameworks for addressing cyberattacks targeting businesses and other organizations. While the Cyber Kill Chain addresses cyberattack processes with a high-level overview, MITRE ATT&CK enables companies with more granular information about cyber attacks.
MITRE ATT&CK was designed to gain intelligence about cyber threats and provide a standard reference and vocabulary for different cyberattacks. It’s a free and open resource that organizes cybersecurity information from around the web into a simple hierarchical framework. Plus, each level of the framework offers detailed procedures to follow depending on various attack techniques so that professionals at all skill levels can provide their organizations with a secure environment.
On the other hand, the Cyber Kill Chain claims that cyberattacks tend to follow the same techniques and strategies every time. This isn’t the case, and new attack vectors and methods are being discovered as technology evolves. MITRE ATT&CK is not a sequence of attack and defense tactics; it’s an extensive knowledgebase that provides cybersecurity professionals with actionable information to deal with specific attack types from experts in their field.
BlackBerry’s suite of Cylance cybersecurity solutions was 100 percent successful in preventing both the Wizard Spider and Sandworm attack emulations very early in MITRE ATT&CK's 2022 evaluation—before any damage occurred.
BlackBerry’s CylancePROTECT® and CylanceOPTICS® solutions provided comprehensive detections on individual attack techniques with high confidence, helping to reduce wasted resources spent chasing false positives.