What Is Cyber Threat Intelligence?
Threat actors thrive in environments where they can operate unnoticed—and, therefore, unimpeded. Threat intelligence helps shine a light on their actions, allowing organizations to prepare for and respond to cyberattacks more effectively. This is beneficial for several reasons:
- Increased visibility into both your ecosystem and the threats it faces
- More effective, data-driven decision-making regarding risk and threat management
- A security strategy built on a solid understanding of common tactics, techniques, and procedures leveraged by threat actors.
- Improved agility and flexibility when responding to cyber threats
- Better overall cyber resilience
- Reduced security costs
- More efficient security operations
Why Cyber Threat Intelligence Is Important
The agility, flexibility, and efficacy of actionable threat intelligence are increasingly critical. Cyberattacks are not only more numerous than ever but also execute far faster. Threat actors—particularly financially motivated, state-sponsored ransomware operators—are increasingly sophisticated.
Even unsophisticated, non-technical cybercriminals can cause serious harm to an organization. Rather than leveraging their own tools and tactics, they can rent cyberattack infrastructure from more sophisticated threat actors. Alternatively, they can buy their way into a compromised system via an initial access broker (IAB).
Threat intelligence requires more than passive data orchestration. An organization must have the necessary infrastructure to continuously monitor its entire ecosystem and the capacity to analyze and contextualize threat data in real time. For most organizations, this means that threat intelligence requires some degree of automation—the volume of information generated by unfiltered threat intelligence feeds is beyond the scope of even the best-equipped security team to consider.
Organizations must also integrate threat intelligence with other processes, such as incident response and risk management. Threat intelligence does not exist in a vacuum; it must be part of an overall approach to cybersecurity.
This also means that any solutions with which you gather threat data—such as an Extended Detection and Response (XDR) solution or a Security Information and Event Management (SIEM) platform—must be fully integrated into your security stack.
The Cyber Threat Intelligence Life Cycle
The threat intelligence lifecycle is the process by which an organization gathers and examines raw data about potential threats and then uses that data to address those threats proactively. The core processes and techniques by which this is achieved are not unique to the cybersecurity sector. Rather, they’ve been developed and honed over multiple decades within the public sector, particularly in military and law enforcement.
In the context of cybersecurity and cyber threat management, this intelligence cycle consists of the following phases:
1. Requirements and Direction. This is where an organization lays the initial groundwork for its threat intelligence program, defining:
- The assets and processes that need to be protected
- The impact of an attack on each asset or process
- How each asset and process should be prioritized in terms of cybersecurity measures
- Why threat actors might target these items, i.e., their motivations
- The full scope of the organization’s attack surface
- The type of threat intelligence required to protect this attack surface and how that data will be used
2. Collection. At this stage, information is gathered from a wide array of internal and external sources. This could include antivirus logs, web traffic, industry feeds, and surface and deep web monitoring.
3. Processing. Much of the data collected in stage two is unfiltered and unformatted—before it is usable, it must first be processed and organized. Given the sheer volume of data collected by even a modest threat intelligence program, it is rarely feasible to do this manually.
4. Analysis. Human personnel examine the processed data, applying their knowledge, intuition, and expertise to contextualize information further. They then determine how best to leverage the insights gained from threat data.
5. Dissemination. Having defined core insights and action items from collected threat data, the threat intelligence team deploys this information to key organizational stakeholders, who then use it to guide their decision-making.
6. Feedback. Having received the finalized threat reports from the intelligence team, stakeholders then circle back to collaborate on any adjustments they feel must be made.
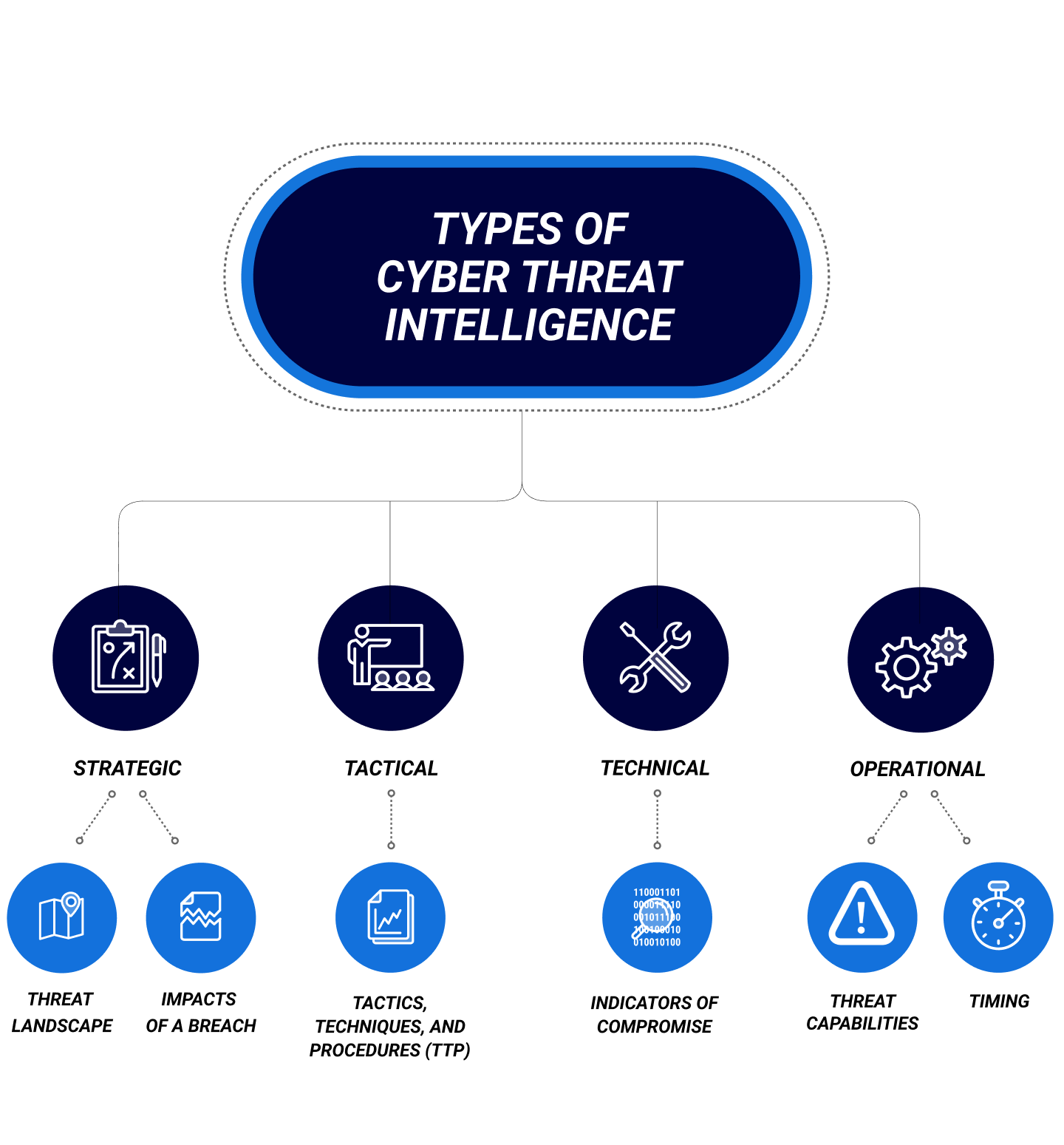
Types of Cyber Threat Intelligence
Strategic Cyber Threat Intelligence
Tactical Cyber Threat Intelligence
Technical Cyber Threat Intelligence
Operational Cyber Threat Intelligence
Use Cases for Cyber Threat Intelligence
The use cases for cyber threat intelligence are quite broad and include the following:
- Actively hunting for and mitigating threats
- Enriching and categorizing security alerts
- Developing a long-term security roadmap
- Assessing an organization’s threat level, security posture, and risk tolerance
- Deploying and configuring new security controls
- Post-incident cyber forensics
- Understanding emerging threat actors and advanced persistent threats and taking preventative action against them