What Is Cuba Ransomware?
Cuba ransomware, AKA Fidel, was first discovered in late 2019 and rose to prominence in 2022. Cuba’s impact doubled year-over-year, compromising hundreds of victims—in 2022, it collected more than $60 million in ransom, prompting CISA and the FBI to issue flash alerts. Cuba ransomware’s official Tor-dot-onion-based website features a Cuban nationalist theme despite intel pointing to the group’s Russian membership: communications contain typical Russian misspellings. Cuba ransomware is affiliated with the small but disproportionately high-impact threat actors RomCom and Industrial Spy.
Cuba’s use of standard commercial software packing techniques is considered less sophisticated than state-sponsored malware, indicating Cuba is likely the product of a small but talented group of profit-seeking individuals. “Packing” refers to compressing software and required libraries into a single binary executable that is difficult to reverse-engineer or detect by antivirus scanners.
Cuba is deployed selectively using a big game hunting strategy, targeting a few high-profile organizations in financial services, government, healthcare, critical infrastructure, and IT sectors. Reports indicate that Cuba operators reliably deliver a decryption package to decrypt victims’ files when ransom is paid but that they also employ a double-extortion tactic and are known to publish the stolen data and documents of victims that refuse to pay.
Latest Cuba Ransomware News
- Cuba Ransomware Gang Continues to Evolve with Dangerous Backdoor (Dark Reading)
- Cuba Ransomware Deploys New Tools: Targets Critical Infrastructure Sector in the U.S. and IT Integrator in Latin America (BlackBerry Blog)
- Cuba Ransomware Claims Cyberattack on Philadelphia Inquirer (BleepingComputer)
- RomCom Threat Actor Abuses KeePass and SolarWinds to Target Ukraine and Potentially the United Kingdom (BlackBerry Blog)
Cuba is often dropped via first-stage Hancitor loader malware, which gains access through phishing attacks, exposed vulnerabilities, or stolen or brute-forced RDP credentials. To lock targets out of their files, Cuba uses the symmetric encryption algorithm ChaCha20 and then appends and encrypts the decryption key using an RSA public key for which they hold the matching private key.
The various tools, tactics and techniques observed in Cuba attacks are noteworthy. Here is a non-exhaustive list of Cuba’s tactics and techniques:
- Communicating to command and control (C2) servers via SystemBC malware that uses SOCKS5 connections
- Leveraging Microsoft Exchange vulnerabilities to penetrate network mail servers
- Moving laterally through a network using a PowerShell, SystemBC, Mimikatz, Cobalt Strike platform, and built-in tools such as cmd.exe
- Use PSEXEC to transfer the payloads to newly compromised systems
- Removing network share access controls
- Creating new users on the compromised system for persistent access
- Altering firewall rules to allow port 3389 for RDP connections
- Disabling Endpoint Detection and Response (EDR) and antivirus security products
- Exploiting Windows Common Log File System (CLFS) driver to steal admin credentials
- Using custom downloader BUGHATCH, antimlaware killer BURNTCIGAR, and Metasploit frameworks to attack systems
- Evading defenses and bypassing security using the Bring Your Own Vulnerable Driver (BYOVD) technique
- Exploiting the vulnerabilitiy CVE-2023-27532 via the Veeam Backup Service to access stored credentials
Signs of a Cuba Ransomware Attack
CISA and the FBI have released indicators of compromise (IOCs) to help identify Cuba’s various payload components, including commonly used filenames and installation paths, C2 IP addresses, and hash signatures. Cuba places component files in the Windows temp directory (C:\windows\temp) and ASP.NET root folder (C:\inetput\wwwroot\aspnet_client) and uses many executable file types:
- ASP.NET (.aspx)
- PowerShell (.ps1)
- Batch scripts (.bat)
- Dynamic Link Libraries (.dll)
- Binaries (.bin)
Cuba’s files may also be named using the last octet of the compromised host’s IP address, e.g., 253.ps1 and 253.bat on a system with the IP address 192.168.1.253.
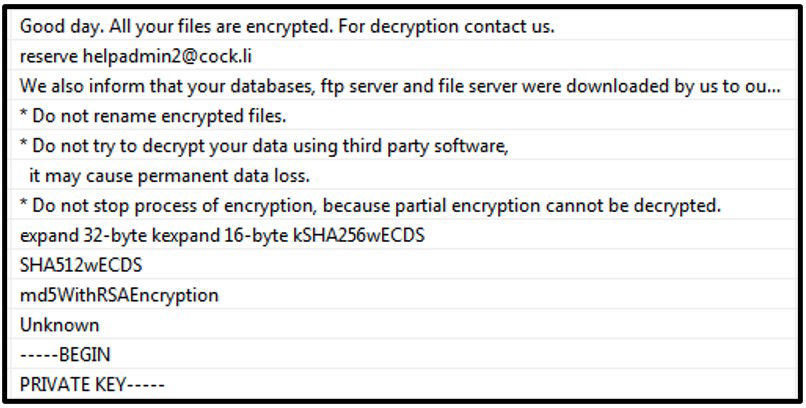
After Cuba encrypts a victim’s files, it appends a .cuba file extension and creates a file named “!!FAQ for Decryption!!.txt” in every folder. The ransom note contains a brief message and an email address to initiate communication with the attackers.
How to Prevent a Cuba Ransomware Attack
Cuba ransomware uses multiple attack techniques, so a Defense in Depth approach is advised for combatting this vicious adversary. Defensive measures that can be employed to combat Cuba ransomware attacks include:
- Password policies mandating strong keyspace and enabling multi-factor authentication for all critical services
- Modern Identity and Access Management (IAM) tools
- Advanced endpoint security products on all endpoints to detect indicators of compromise (IOC) and take defensive action to block malicious payloads from executing
- Keeping all operating systems and software up to date and conducting regular vulnerability scanning and penetration testing of all network infrastructure, remediating any discovered vulnerabilities as soon as possible
- Implementing a principle of least privilege approach to security, including removing unnecessary access to administrative shares and other services
- Segmented networks and NIPS and NIDS to monitor network activity for anomaly behavior
- Hardening all endpoints, including employee workstations and servers, by disabling command-line and scripting activities and permissions and unrequired services to reduce the potential of a living off the land (LOTL)-type attacks
- A solid backup strategy that includes offline, encrypted, and immutable backups of data