What Is a DDoS Attack?
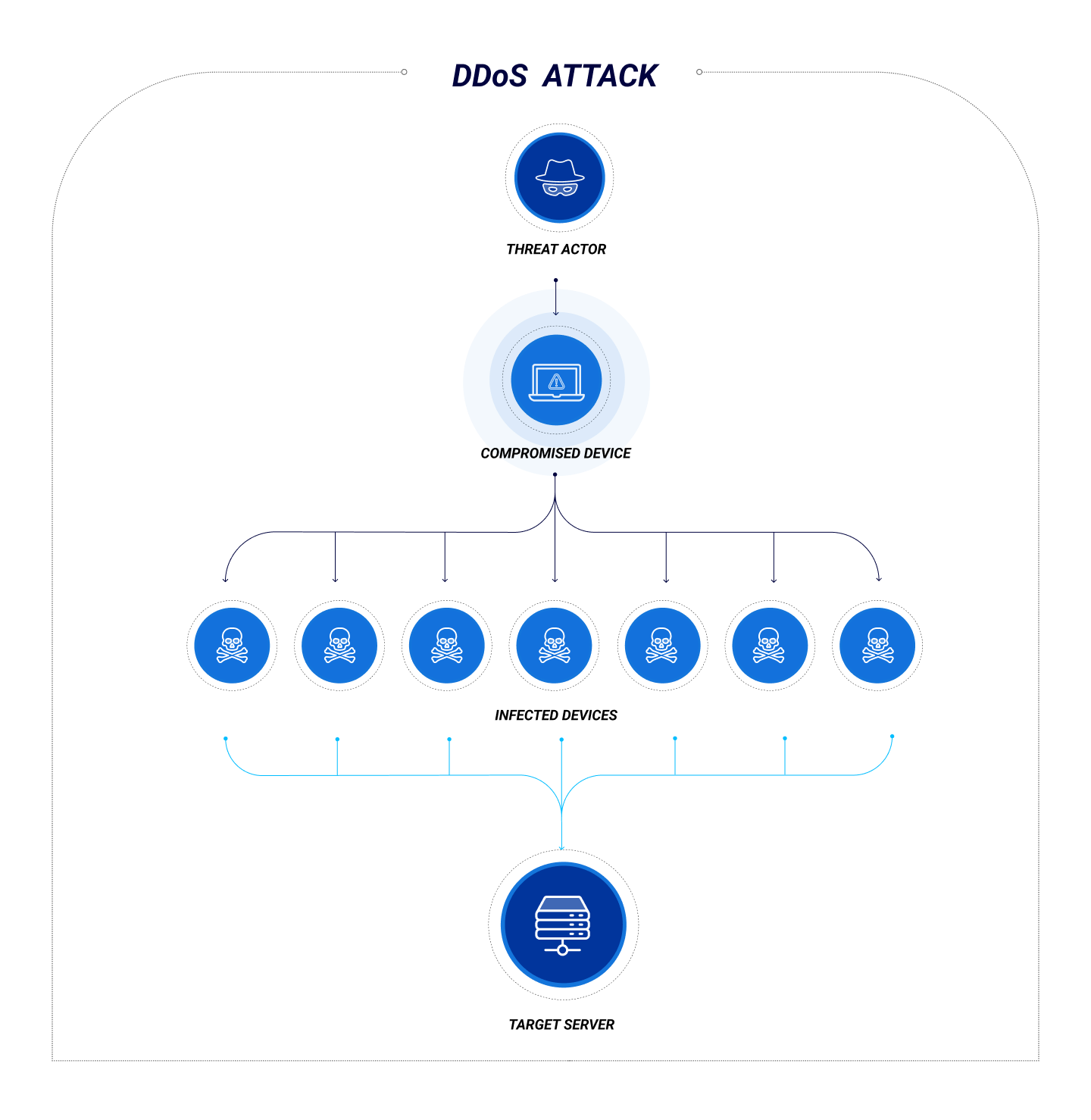
A Distributed Denial-of-Service (DDoS) attack is a cyberattack that kicks legitimate users out of system resources. First, the attackers steal credentials to access the system and infect devices with malware. The malware allows unauthorized users to remotely control devices and create a group of bots that carry out the attacker’s ill intentions.
Once a botnet is established, attackers flood the targeted network with so much traffic that the computer crashes and prevents authorized users from accessing the resources.
Type of DDoS Attacks
1. Application Layer Attacks
2. Protocol Attacks
3. Volumetric Attacks
Cost of a DDoS Attack
DDoS attacks are like a hostile takeover. Attackers gain access to your systems, data, and devices and lock legitimate users out of network resources. DDoS attacks can cost organizations significant amounts of time and money to recover from, not to mention reputational damage and downtime.
According to a recent report, small businesses could end up paying more than $100,000 to recoup their systems and data following a DDoS attack; larger companies can expect to pay $2 million per incident. However, there are steps that organizations can take to detect DDoS attacks and minimize their damage.
The most effective ways to stop DDoS attacks are to improve your cyber resiliency and increase your threat intelligence-gathering capabilities.
Adopt an advanced Zero Trust Network Access (ZTNA) infrastructure. A cloud-native ZTNA solution that incorporates strong endpoint protection capabilities provides protection, detection, and prevention against DDoS attacks.
Subscribe to a DDoS protection service. A service such as AWS Shield monitors traffic, identifies attacks, and mitigates their impact by rerouting malicious traffic away from your network.
Configure your network to support anycast network diffusion. Incorporating anycast routing improves network flexibility by distributing inward-bound traffic across multiple servers.
Conduct routine penetration (pen) testing audits..Regularly practicing your organization’s DDoS response plan with all stakeholders during a simulated attack helps identify gaps and issues.
Support social media intelligence gathering efforts. Monitor social media, particularly Twitter, for threats, conversations, and boasts that may indicate that you have been targeted.