Combating Fileless Attacks
BlackBerry AI-driven threat prevention and response solutions protect you from threats, no matter how they operate
Combating fileless attacks requires a departure from traditional, file-based countermeasures. BlackBerry uses memory defense, script and macro control, and our Context Analysis Engine (CAE) to keep your organization safe.
Hacking Exposed Demo from RSA - Examples of Fileless Threats

See how recent threats – including fileless attacks – operate in the wild
The replay of our Hacking Exposed demo at RSA illuminates the tools and techniques of memory-based, fileless, script-based, and app-based attacks, and more.

Threat Spotlight: Kovter Malware Fileless Persistence Mechanism
Join us as we take a closer look at Kovter, a pervasive click-fraud trojan that uses a fileless persistence mechanism to maintain a foothold in an infected system.

DirtySecurity Podcast: Memory-Based Attacks and How To Stop Them
In this episode of DirtySecurity, we chat with security engineer Josh Fu about fileless attacks - why they're so prevalent, how they work, and how to prevent them.
Prevention - BlackBerry Protect
Memory Exploitation Detection and Prevention
Add an additional layer of security and strengthen the OS’s basic protection features – preventing attackers from using memory to exploit vulnerabilities.
Script and Macro Management
Monitor, detect, and protect against malicious scripts and/or script paths that may be running in your environment – before they can execute.
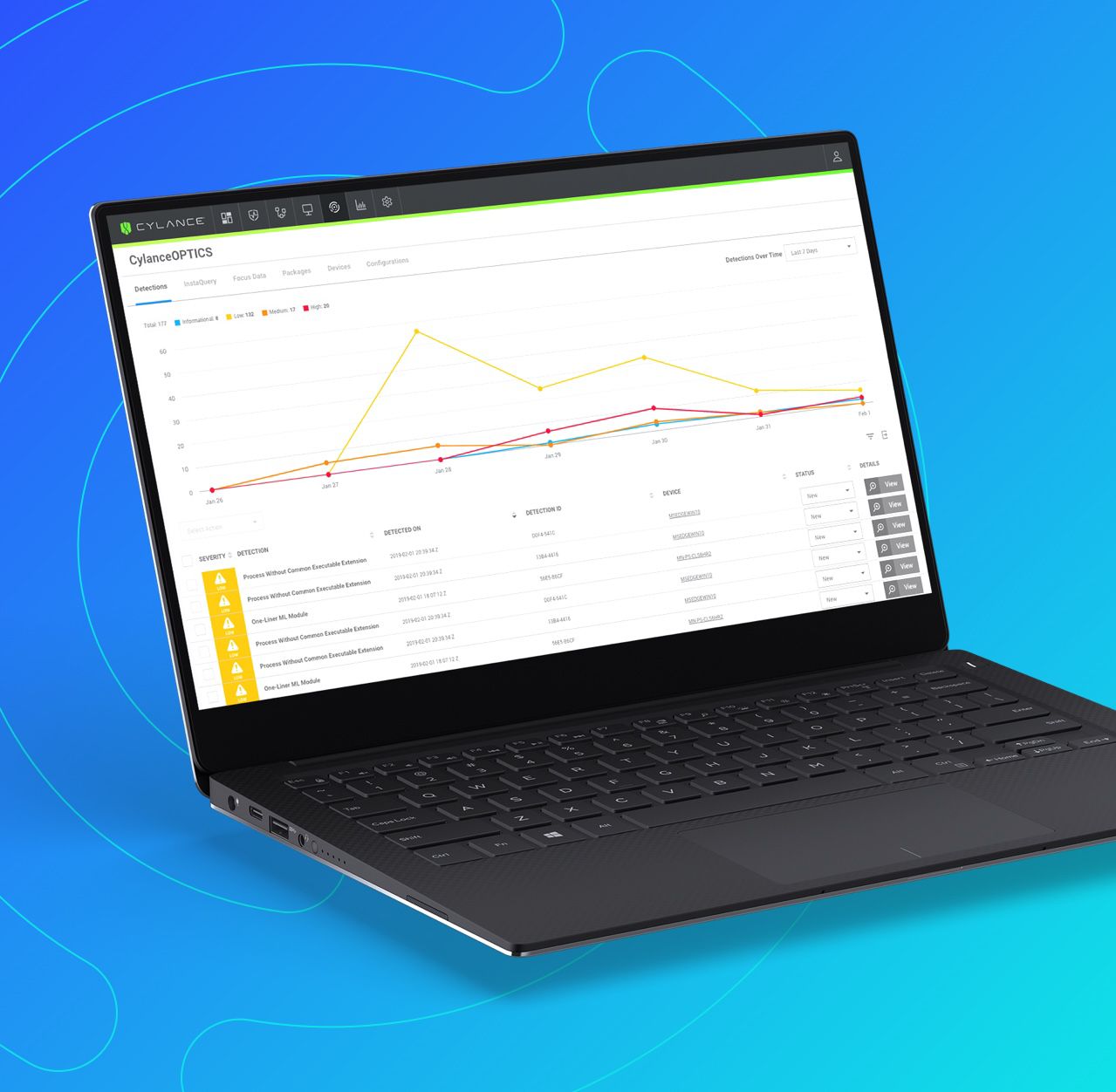
Response - BlackBerry Optics
Powering Dynamic Threat Detection and Automated Response
Our approach pushes the threat detection and response to the endpoint, allowing every endpoint in your organization to act as a virtual SOC, dynamically detecting threats and taking response actions around the clock and without human intervention.
Resources


